Helix C2: Modular & Evasive C2 Framework
A modular command and control framework with randomized request chunking for IDS evasion. Designed to be educational, open source, and simpler than Mythic C2.

What is Helix C2?
A modular command and control framework designed to be simpler than Mythic C2 while maintaining flexibility. Built for rapid experimentation and learning.
Helix C2 Status: In Development
Preview
Features & Design Philosophy
Open Source & Educational Focus
All code will be made public with detailed documentation and heavy commenting, enabling anyone to understand and build upon it as a foundation for their own agents.
Key Principles:
- Open source with detailed documentation
- Heavily commented code for educational purposes
- Balance between simplicity and functionality
- Modular architecture for customization
Use Cases:
- Framework is modular and intuitive for red team operations
- Can be quickly customized for diverse assessment needs
- Suitable as educational foundation and for advanced use cases
Evasion Features
To prevent detection by intrusion detection systems (IDS), Helix C2 implements:
- Randomized Request Chunking: Requests are split into random-sized chunks, making it impossible to fingerprint request sizes based on patterns
- Dynamic Size Variation: Each transmission varies in size, reducing the risk of signature-based detection while maintaining data integrity
- (More features will be added as development continues)
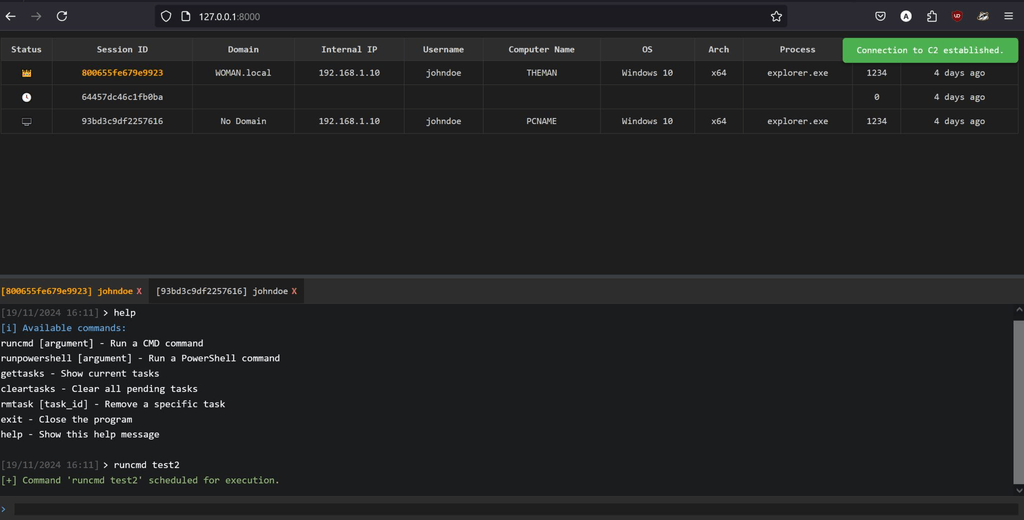
Dashboard UI
The base dashboard UI is designed to be clear and intuitive, helping operators quickly focus on what matters most.
Status Indicators:
- 👑 = Admin privileges
- 💻 = Active/connected agent
- 🕐 = Registration in progress
More updates coming as development continues