Store, Read, and Convert Shellcode in .bin and C Arrays: C++ and xxd
Learn to store and read shellcode in .bin files using C++, and quickly convert between .bin files and C arrays with xxd.

Working with binary files is a fundamental skill in malware development. Whether you’re storing shellcode, encrypting payloads, or integrating binary data into your projects, you need to know how to work with .bin files and C arrays.
Despite being essential, many online resources skip over these basics or assume you already know them. This post covers two approaches:
- C++ code for storing and reading
.binfiles in your programs: - xxd on Linux for quick conversions between .bin files and C arrays:
Storing shellcode in .bin files (C++)
Output
Code
#include <iostream>
int main(int argc, char *argv[]) {
// Check for the correct number of arguments
if (argc < 2) {
printf("Usage: %s <output_filename>.bin\n", argv[0]);
return 1;
}
// Define the variables
char* output_file = argv[1];
unsigned char shellcode[] = {0x99, 0x12, 0x15, 0x0C}; // Your shellcode goes into here.
// Open a binary file for writing
FILE *file = fopen(output_file, "wb");
if (file == NULL) {
perror("Error opening file");
return 1;
}
// Write the shellcode to the file
fwrite(shellcode, sizeof(shellcode), 1, file);
// Close the file
fclose(file);
printf("Shellcode written to %s\n", output_file);
return 0;
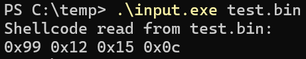
}Reading .bin files to retrieve shellcode (C++)
Output
Code
#include <iostream>
int main(int argc, char *argv[]) {
// Check for the correct number of arguments
if (argc < 2) {
printf("Usage: %s <input_filename>.bin\n", argv[0]);
return 1;
}
// Define the variables
char* input_file = argv[1];
// Open the binary file for reading
FILE *file = fopen(input_file, "rb"); // Opens file with read-mode "rb". "rb" is used for non-text files, while "r" is used for text files.
if (file == NULL) {
perror("Error opening file");
return 1;
}
// Find the size of the file
fseek(file, 0, SEEK_END); // moves the file pointer to the end of the file.
long fileSize = ftell(file); // retrieves the current file pointer position, which is the size of the file.
fseek(file, 0, SEEK_SET); // moves the file pointer back to the start so that subsequent read or write operations start from the beginning of the file.
// Allocate memory to hold the shellcode
unsigned char *shellcode = (unsigned char *)malloc(fileSize);
if (shellcode == NULL) {
perror("Memory allocation failed");
fclose(file);
return 1;
}
// Read the shellcode from the file and store it in the "shellcode" variable
fread(shellcode, fileSize, 1, file);
// Close the file
fclose(file);
// Print the shellcode as hexadecimal values
printf("Shellcode read from %s:\n", input_file);
for (long i = 0; i < fileSize; i++) {
printf("0x%02x ", shellcode[i]);
}
printf("\n");
// Free the allocated memory
free(shellcode);
return 0;
}Convert .bin files to C-Style Arrays (xxd)
For quick conversions between .bin files and C arrays (like converting a .bin payload to use in your code), you can use the xxd tool from the command line.
xxd -i file.bin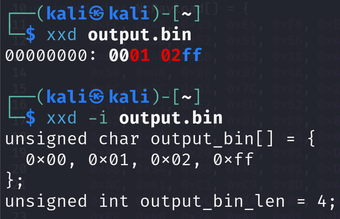
Convert C-Style Arrays to .bin files (xxd)
You can also perform the reverse conversion, using sed and tr to transform text files containing C-style arrays back into binary files:
cat input.txt | tr -d ' \n' | sed -n 's/.*{ *\([^}]*\) *}.*/\1/p' | xxd -r -p > output.bin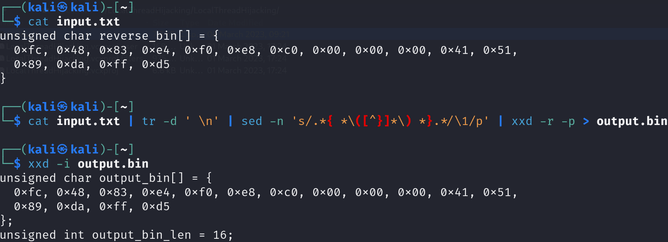
Conclusion
Now you have multiple approaches for working with shellcode in binary files:
- C++ methods for when you need programmatic control and integration into larger projects.
- xxd on Linux for quick conversions between binary files and C-style arrays.
Each approach has its place in your malware development workflow. Hope you learnt something new with this! Happy Hacking!