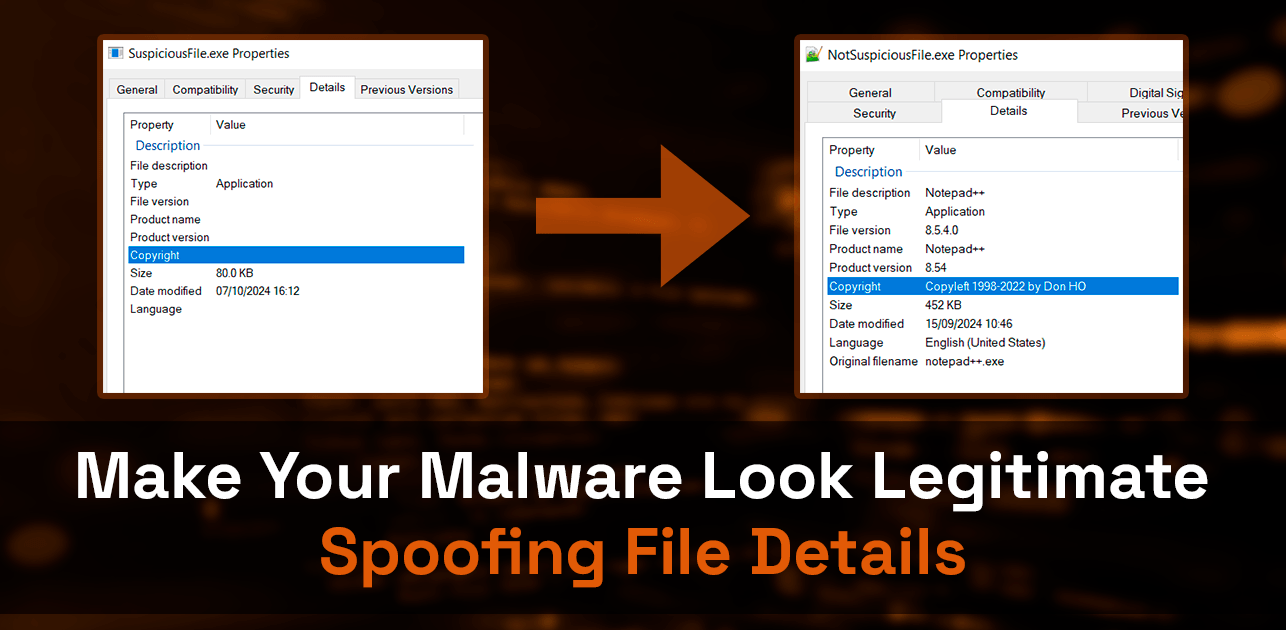
Make Your Malware Look Legitimate: Spoofing File Details
Learn how to make your malware appear as legitimate software by adding an icon to your malware, and copying file properties from real programs.
Why Spoof File Properties?
When you right-click a file and check its “Details” tab, you see information like the company name, product version, and description.
By copying these properties to your malware, you make it look less suspicious to both users and security tools. Instead of appearing as an unknown executable, your file can look like it came from Microsoft, Google, or any trusted company.
Adding Spoofed Metadata in Visual Studio
- Add a New Item to Your Project
- Right-click the project, select
'Add' > 'New Item' -
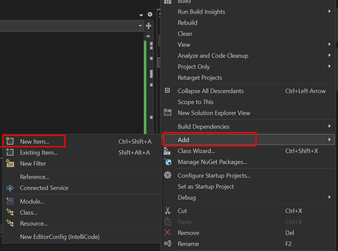
- Right-click the project, select
- Add a Resource (
.rc) File- Select “Resource File (.rc)” and optionally rename it to
metadata.rc. -
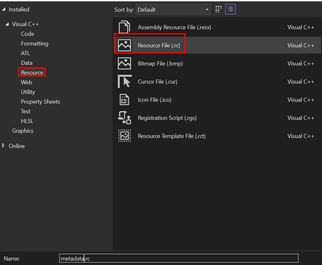
- Select “Resource File (.rc)” and optionally rename it to
- Exit Resource Viewer
- Visual Studio will automatically open the resource viewer. Close it by clicking the ‘X’ - we’ll edit the file as text instead.
-
- Open the File as Text
- Right-click the resource file, and select
'Open With' > 'Source Code (Text) Editor'. -
-
- Right-click the resource file, and select
- Insert the Metadata
- Scroll to the bottom of the file and paste this code. Modify the values to match whatever legitimate program you want to impersonate:
1 VERSIONINFO
FILEVERSION 112, 0, 5615, 88 // File version separated by commas
PRODUCTVERSION 1, 0, 0, 0
FILEFLAGSMASK 0x0L
#ifdef _DEBUG
FILEFLAGS 0x1L
#else
FILEFLAGS 0x0L
#endif
FILEOS 0x0L
FILETYPE 0x0L
FILESUBTYPE 0x0L
BEGIN
BLOCK "StringFileInfo"
BEGIN
BLOCK "040904B0"
BEGIN
// Modify the values below to match your target program
VALUE "CompanyName", "Google LLC."
VALUE "FileDescription", "Google Chrome"
VALUE "InternalName", "Chrome"
VALUE "LegalCopyright", "Copyright 2023 Google LLC."
VALUE "OriginalFilename", "chrome.exe"
VALUE "ProductName", "Google Chrome"
VALUE "ProductVersion", "112.0.5615.86"
END
END
BLOCK "VarFileInfo"
BEGIN
VALUE "Translation", 0x409, 1200
END
ENDExtract File Properties from Any Program
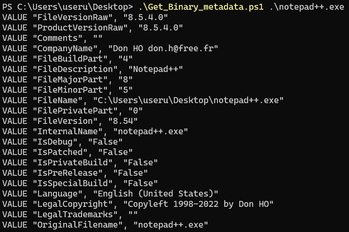
The example above uses Chrome’s file properties. To copy properties from any legitimate program (including DLLs), use this PowerShell script:
# Usage: .\script.ps1 "C:\Path\To\Program.exe"
$path = $args[0]
# Get the file version information
$file = Get-Item $path
$versionInfo = $file.VersionInfo
# Print all properties in the format needed for the .rc file
foreach ($property in $versionInfo.PSObject.Properties) {
Write-Output "VALUE `"$($property.Name)`", `"$($property.Value)`""
}Save this as extract-metadata.ps1 and run it with:
.\extract-metadata.ps1 "C:\Program Files\Google\Chrome\Application\chrome.exe"Copy the output and paste the relevant values into your resource file.
Now, your malware will have the same file properties as the legitimate program.
Adding Icon to Binary
It’s also possible to give the binary an icon, which again is a step towards making the binary appear less suspicious.
Before adding, lets extract an icon from an executable:
Extracting Icons from EXE
- Right-click target executable.
- Select
7-Zip > Open archive. - Select the folders
.rsrc > ICON -
- In the ICON folder, you have all the icons from the executable:
-
Add Icon to Binary
The steps to add an icon to a binary are shown below.
.icoFile Placement- Place the
.icofile in the same location where the.slnfile is located. -
- Place the
- Modify The Resource File
- In the resource file, insert the following line:
IDI_ICON1 ICON "<filename>.ico"- Build the solution and the binary should now have an icon.